Information Security Services
- Penetration Testing
- Vulnerability Assessment
- ISMS Policy Templates
- ISO 27001 Consultancy
- BCP & DR Consultancy
- IT Audit consultancy
- SIEM Solutions
- Virtual Private Network
- Email Security
- Data Protection
- Network Security
- System Security
Do you want to protect your systems and network?

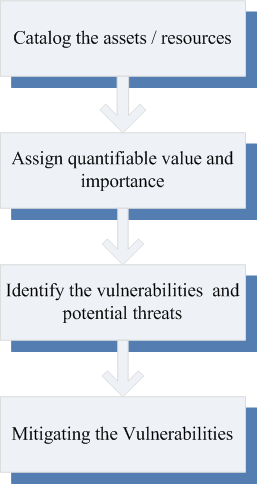
Ways to reduce vulnerability
- Constant vigilance
- Proper system maintenance
- Best practices in deployment
- Development and deployment lifecycle
- Auditing
_________________________
Vulnerability Scanners
- Nessus
- GFI LANguard
- Retina
- Core Impact
_________________________
iSquare Pentesting Process
iSquare Systems - Vulnerability Assessment Test
What is a Vulnerability?
-
Vulnerability is a weakness which allows an attacker to reduce a information assurance.
A weakness or lack of a safeguard that can be exploited by a threat, causing harm to the information systems or networks
Pentesting vs Vulnerability Assessment
Pentesting |
Vulnerability Assessment |
|
|
How the vulnerability occurs?
-
Systems are shipped with known and unknown security holes and bugs with insecure default settings of OS, Databases and Passswords.
-
System or Network misconfigurations by administrators.
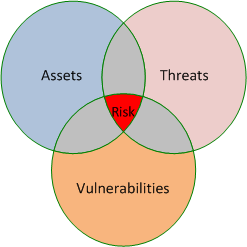
What is Risk, Vulnerability and Threat?
To protect the internal or customer’s data, it is must to understand the risks and vulnerabilities affecting the systems.
Threat: An event or activity that has the potential to cause harm to the information systems or networks
Vulnerability: A weakness or lack of a safeguard that can be exploited by a
threat, causing harm to the information systems or networks
Risk. The potential for harm or loss to an information system or network; the
probability that a threat will materialize
Vulnerabilities Classification
- Hardware
- Software
- Network
- Personnel
- Site
- Organizational
Examples of Software vulnerabilities
- Buffer overflows
- SQL injection
- Code injection
- Directory traversal
- Cross-site scripting in web applications
- HTTP header injection
- HTTP response splitting
What is SQL Injection?
- SQL injection is a technique that takes advantage of non validated input vulnerabilities to pass SQL commands through a web application for execution by a backend database
_____________________________________________________
- Self assessment planning
- Risk (event) identification
- Risk assessment
- Risk response
- Avoid Risk
- Reduce Risk
- Accept Risk
- Transfer Risk
iSquare - Risk Management Process
Risk Self Assessment
Risk Mitigation Methods