Information Security Services
- Penetration Testing
- Vulnerability Assessment
- ISMS Policy Templates
- ISO 27001 Consultancy
- BCP & DR Consultancy
- IT Audit consultancy
- SIEM Solutions
- Virtual Private Network
- Email Security
- Data Protection
- Network Security
- System Security
Do you want to protect your systems and network?
VPN
A virtual private network (VPN) is a computer network that uses a public telecommunication infrastructure such as the Internet to provide remote offices or individual users with secure access to their organization's network.
Advantages:
- Low cost
- Secured
- High encryption
_________________________
Single Sign On - SSO
Single Sign On (SSO) is a mechanism that allows a user to be authenticated only once on a system.
Advantages:
- Once authenticated, user can roam the network freely and access resources and services without being re challenged for authentication.
- Easier administration by reducing the number of locations on which an account must be defined
- Enabled through authentication systems that provide logon credentials automatically when prompted.
SSO Methods:
- Scripts
- Kerberos
- SESAME
- KryptoKnight
_________________________
E-Mail Security
Email is one of the most widely and commonly used Internet services Methods to improve Email Security
- Restricting access to messages to their intended recipients
- Maintaining the integrity of messages
- Authenticate and verify the source of messages
- Verify the delivery of messages
- Classify sensitive content within or attached to messages
- Provide for non repudiation
_________________________
iSquare Systems Information Security Consulting
To protected information and information systems from unauthorized access, use, disclosure, disruption, modification or destruction.
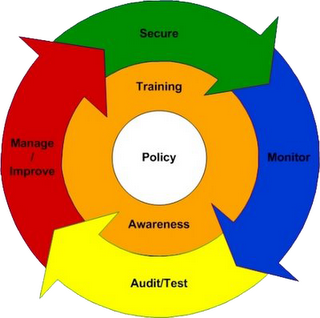
ISMS – Information Security Management system
To Establish, implement, operate, monitor, review , maintain and improve information security.
- ISQS-ISMS-001 ISMS Handbook v1.x.pdf
- ISQS-ISMS-002 ISMS Scope Statement v1.x.pdf
- ISQS-ISMS-003 ISMS Scope v1.x.pdf
- ISQS-ISMS-004 Risk Assessment and Treatment.pdf
- ISQS-ISMS-005 Risk Assessment Methodology v1.x.pdf
- ISQS-ISMS-006 SOA- Statement of Applicability v1.x.pdf
- ISQS-ISMS-007 Information Security Policy v1.x.pdf
- ISQS-ISMS-008 Information Risk Management Policy v1.x.pdf
- ISQS-ISMS-009 Remote Access Policy and Procedure v1.x.pdf
- ISQS-ISMS-010 Risk Acceptance v1.x.pdf
- ISQS-ISMS-011 Information Exchange Policy v1.x.pdf
- ISQS-ISMS-012 Clear Desk and Clear Screen Policy v1.x.pdf
- ISQS-ISMS-013 Disaster Recovery and Data Backup Policy v1.x.pdf
- ISQS-ISMS-014 Anti Malicious Code Policy v1.x.pdf
- ISQS-ISMS-015 Incident Management Policy v1.x.pdf
- ISQS-ISMS-016 Acceptable Use Policy v1.x.pdf
- ISQS-ISMS-017 Information Classification Policy and Procedure v1.x.pdf
- ISQS-ISMS-018 Access Control Policy v1.x.pdf
- ISQS-ISMS-019 Anti Virus Procedure v1.x.pdf
- ISQS-ISMS-020 Desktop Security Policy v1.x.pdf
- ISQS-ISMS-021 email Usage Policy v1.x.pdf
- ISQS-ISMS-022 email Retention Policy v1.x.pdf
- ISQS-ISMS-023 Asset Identification and Classification - All v1.x.pdf
- ISQS-ISMS-024 Change Management Procedure v1.x.pdf
- ISQS-ISMS-025 Personal Communication Devices Policy v1.x.pdf
- ISQS-ISMS-026 Virtual Private Network - VPN Policy v1.x.pdf
- ISQS-ISMS-027 Audit Vulnerability Scan Policy v1.x.pdf
- ISQS-ISMS-028 Acceptable Encryption Policy v1.x.pdf
- ISQS-ISMS-029 Information Backup v1.x.pdf
- ISQS-ISMS-030 Hardware and Software Inventory v1.x.pdf
- ISQS-ISMS-031 Image CD for Workstations v1.x.pdf
- ISQS-ISMS-032 Installation of computer Workstations v1.x.pdf
- ISQS-ISMS-033 New LAN Connection v1.x.pdf
- ISQS-ISMS-034 Password Policy v1.x.pdf
- ISQS-ISMS-035 Requirement Analysis and Team Allocation v1.x.pdf
- ISQS-ISMS-036 Software Design v1.x.pdf
- ISQS-ISMS-037 Guidelines for Working in Secure Areas v1.x.pdf
- ISQS-ISMS-038 Software Implementation v1.x.pdf
- ISQS-ISMS-039 Fast Development Track v1.x.pdf
- ISQS-ISMS-040 Rational Change Management v1.x.pdf
- ISQS-ISMS-041 Baseline Catalogue v1.x.pdf
- ISQS-ISMS-042 System Monitoring and Maintenance - Troubleshoot, Planned and Unplanned Maintenance Rev 1.x.pdf
- ISQS-ISMS-043 System Monitoring and Maintenance - Monitoring Systems and Servers Rev 1.x.pdf
- ISQS-ISMS-044 Software Development - Designing Rev 1.x.pdf
- ISQS-ISMS-045 Software Development - Life Cycle Rev 1.x.pdf
- ISQS-ISMS-046 Software Development - Implementation Rev 1.x pdf
- ISQS-ISMS-047 Software Development - Requirement Management Rev 1.x pdf
- ISQS-ISMS-048 Software Development - Rational Change Management Rev 1.x.pdf
- ISQS-ISMS-049 Software Development - Fast Development Track Rev 1.x pdf
- ISQS-ISMS-090 Implementing of New Service Rev 1.x pdf
- ISQS-ISMS-091 Business Enhancement v1.x.pdf
- ISQS-ISMS-092 Training and Development v1.x.pdf
ISMS Policy Templates
______________________________________________________
- Stage 1 – Documentation Review
- Stage 2 – Implementation Audit
iSquare ISO 27001 ISMS Consultancy
ISO 27001 (ISO/IEC 27001:2005)
ISO 27001 is an Information Security Management System (ISMS) standard published in October 2005 by the International Organization for Standardization (ISO) and the International Electro technical Commission (IEC)
ISO 27001 Stages
ISO 27001 usually conducted in at least two stages, both to identify compliance to ISO 27001:2005